Clever Microsoft Local Login Form
Clever Microsoft Phishing Scam Creates a Local Login Form
A clever phishing campaign has been spotted that bundles the scam’s landing page in the HTML attachment rather than redirecting users to another site that asks them to log in.
A typical credential-stealing phishing scam consists of an email where the attacker tries to convince the user to click a link in order to retrieve a document or prevent something from happening. These links will then bring the user to a web site, or landing page, that includes a login form where the user must enter their login credentials to proceed.
With this type of attack, users can either detect the scam by the contents of the email, by a suspicious remote site and landing page, or by alerts from security solutions.
Let’s show login form locally instead
To prevent users from becoming suspicious when they are redirected to a site with a strange domain or URL, a clever scammer decided to generate the phishing scam directly in the user’s browser without going to a remote site.
This new method was noticed by ISC Handler Jan Kopriva, who stated that they received a generic phishing email stating “Please find attached a copy of your payment notification” and containing an HTML attachment named ‘payment.html’.
This attachment is simply an HTML file with a large amount of obfuscated JavaScript, which happens to be the secret sauce for this scam.
Obfuscated JavaScript in payment.html attachment
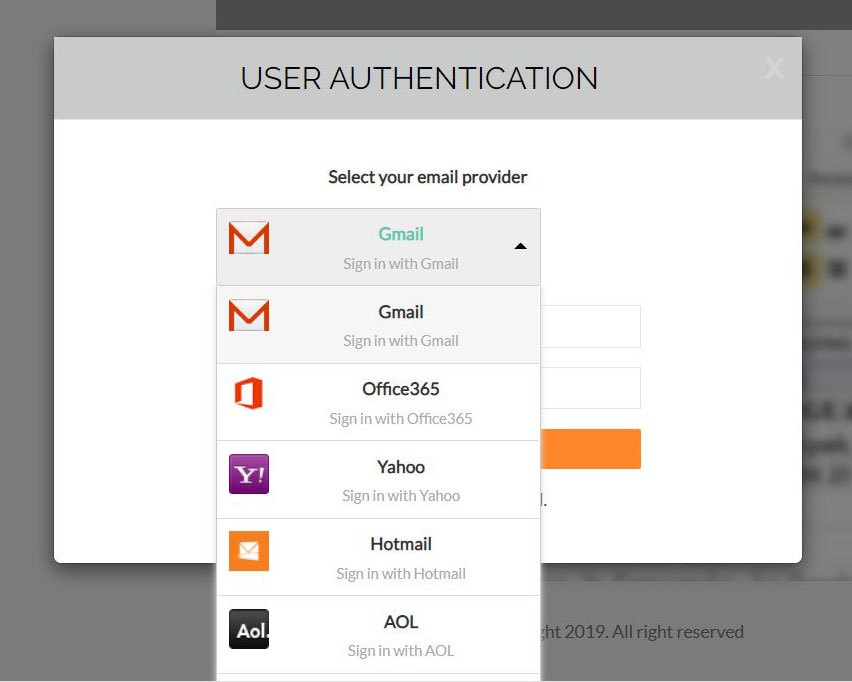
When the user opens the attachment, instead of being redirected to a remote site that contains a login form, the JavaScript renders a ‘Microsoft Docs’ login form directly within the browser as shown below.
This generated form also includes a variety of methods that users can log in to the site, including Gmail, Office365, Yahoo, Hotmail, and Yahoo.
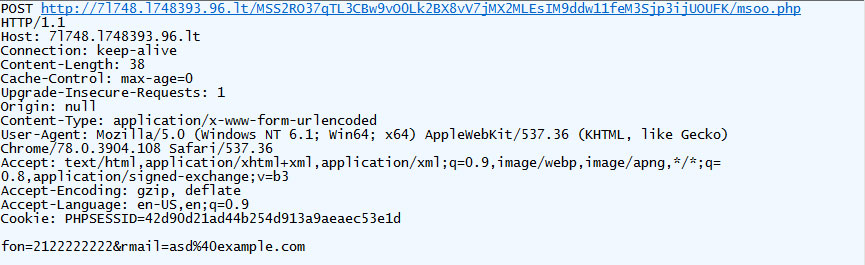
When a user submits information, JavaScript will quietly submit the data to a remote site in the background without the user knowing.
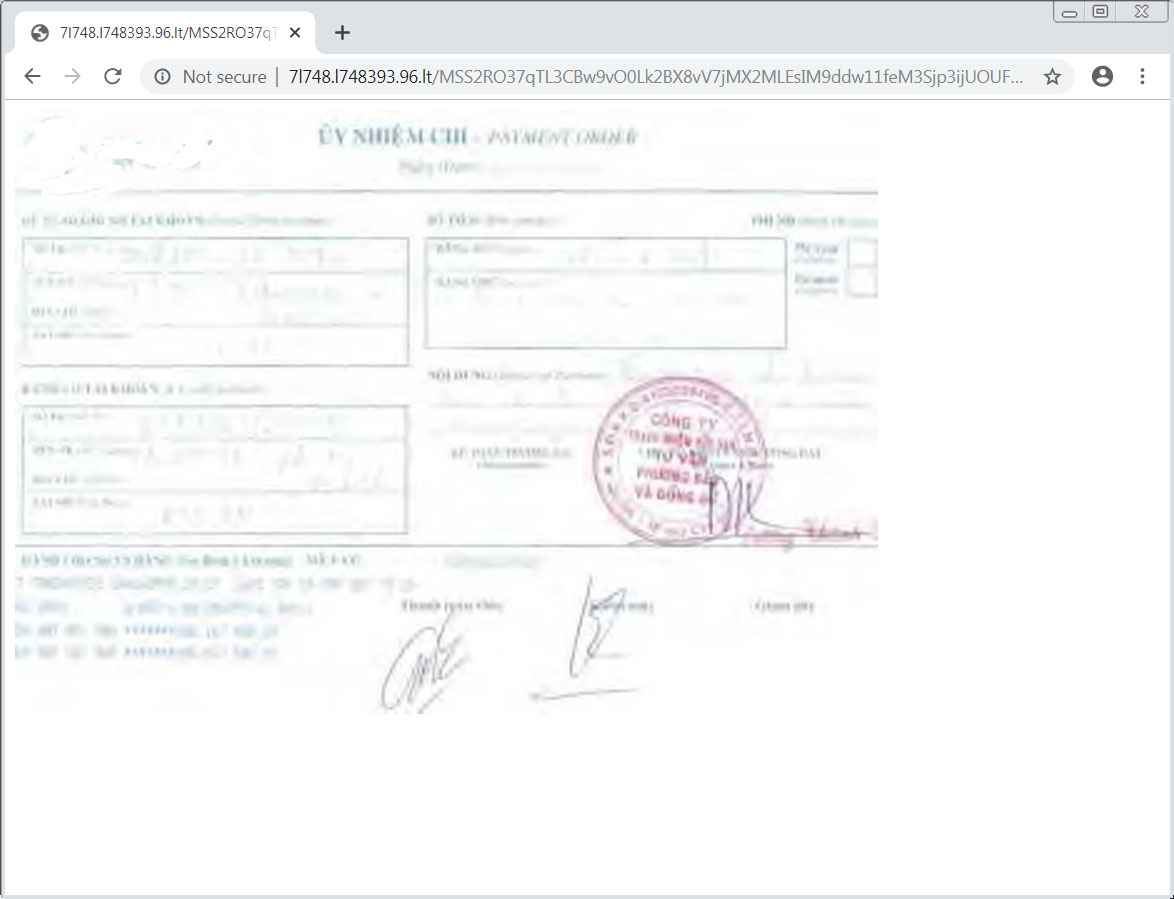
They will then be redirected to a remote site that displays a fake payment notice in the browser. This is a mistake as the payment notice could easily have been generated by the JavaScript and a base64 encoded image contained in the attachment.
At this point, though, it doesn’t matter if the remote site is blocked or deemed suspicious as the attacker has already received the stolen credentials.
As you can see, by generating the login form locally, rather than using a remote site, the attacker does not have to generate realistic-looking domain names and URLs to host their login forms.
Furthermore, by generating the landing page locally, they reduce the risk that their landing page will be discovered and removed.
This is just another tactic that email users will need to be aware of to protect themselves from becoming a victim of a phishing scam.



